What is DDoS Attacks How Can They Be Mitigated?
In today’s digitally connected world, online services are constantly at risk from various types of cyber threats. Among these, Distributed Denial of Service (DDoS) attacks stand out due to their potential to cause significant disruption. A DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. These attacks exploit multiple compromised computer systems, including computers and other networked resources like IoT devices, to generate the attack traffic.
Understanding the characteristics, methods, and impacts of DDoS attacks is essential for any organization reliant on internet connectivity. This article will delve into the nature of DDoS attacks, explore the common techniques used by attackers, assess the potential damage caused by these attacks, and outline effective strategies for mitigation. By comprehensively addressing these aspects, organizations can better prepare and defend against the persistent threat of DDoS attacks, ensuring the availability and reliability of their online services.
What is DDoS Attacks?

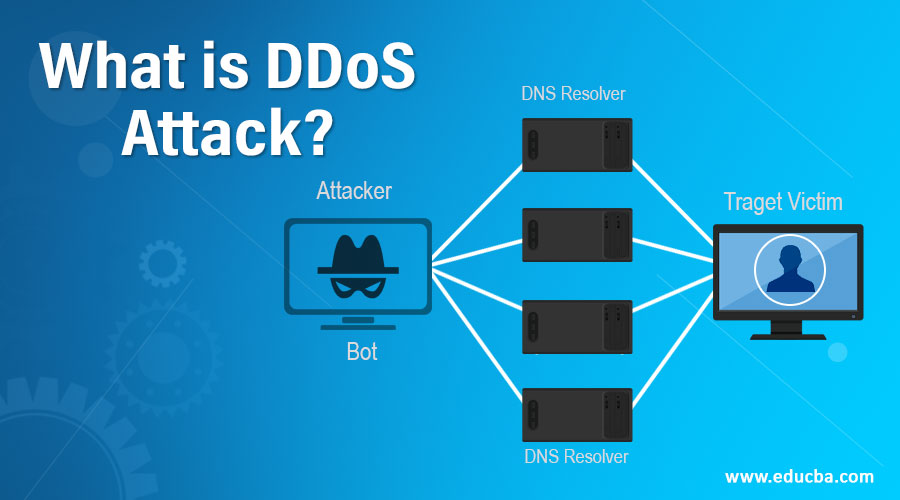
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of internet traffic. These attacks exploit multiple compromised computer systems as sources of attack traffic, which can include computers and other networked resources such as IoT devices.
Key Characteristics of DDoS Attacks:
- Distributed Nature:
- The attack originates from multiple sources, making it difficult to distinguish legitimate traffic from malicious traffic.
- Flooding of Traffic:
- The goal is to saturate the bandwidth or resources of the target system, causing it to slow down or become completely unresponsive.
- Types of DDoS Attacks:
- Volume-Based Attacks: Overwhelm the bandwidth of the target site.
- Protocol Attacks: Exploit vulnerabilities in network protocols.
- Application Layer Attacks: Target specific applications or services on the target system.
Common Methods Used in DDoS Attacks:
- Botnets:
- Networks of hijacked devices (bots) that are used to launch attacks simultaneously.
- Amplification:
- Techniques like DNS amplification where small queries result in large responses directed at the target.
- Reflection:
- Attackers send requests to third-party servers with the spoofed IP address of the target, causing the servers to send responses to the target.
Impact of DDoS Attacks:
- Service Disruption: Legitimate users are unable to access services.
- Financial Loss: Downtime can result in significant revenue loss, especially for e-commerce and other online services.
- Reputation Damage: Extended outages can harm the reputation of the affected organization.
- Mitigation Costs: Significant resources are often required to defend against and mitigate DDoS attacks.
Mitigation Strategies:
- Traffic Analysis and Filtering:
- Using firewalls, routers, and intrusion detection systems to filter out malicious traffic.
- Rate Limiting:
- Limiting the number of requests a server will accept over a certain time period.
- Content Delivery Networks (CDNs):
- Distributing content delivery to mitigate the impact of traffic spikes.
- Anti-DDoS Services:
- Specialized services that detect and mitigate DDoS attacks.
Knowing how to protect against DDoS attacks is important for keeping online services available and reliable.















Hey people!!!!!
Good mood and good luck to everyone!!!!!
Fantastic site Lots of helpful information here I am sending it to some friends ans additionally sharing in delicious And of course thanks for your effort
Hi i think that i saw you visited my web site thus i came to Return the favore I am attempting to find things to improve my web siteI suppose its ok to use some of your ideas
helloI really like your writing so a lot share we keep up a correspondence extra approximately your post on AOL I need an expert in this house to unravel my problem May be that is you Taking a look ahead to see you