How to Use Ettercap in Kali Linux for Network Analysis and Security
Complete Guide to Using Ettercap in Kali Linux for Network Analysis and Security
Introduction
Ettercap is a comprehensive suite for man-in-the-middle attacks on LAN. It features sniffing of live connections, content filtering on the fly, and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis. In this article, we’ll explore what Ettercap is, how it works, and how to use it in Kali Linux.
What is Ettercap?
Ettercap stands for “Ethernet Capture” and is a robust network security tool. It is used to intercept and analyze network traffic. Ettercap allows users to launch various man-in-the-middle (MITM) attacks on a network, making it an essential tool for network administrators and penetration testers. It supports active and passive dissection of numerous protocols and includes features for network and host analysis.
How Does Ettercap Work?
Ettercap works by placing itself between two devices in a network communication flow. This allows it to intercept, log, and manipulate the data being transmitted between these devices. The primary techniques Ettercap uses include:
- ARP Poisoning: Ettercap uses Address Resolution Protocol (ARP) poisoning to intercept traffic on a switched LAN by associating the attacker’s MAC address with the IP address of a target device.
- DNS Spoofing: Ettercap can intercept DNS requests from a target machine and respond with forged DNS responses.
- Packet Injection: Ettercap can inject packets into an existing data stream, allowing for various attack vectors.
Installing Ettercap in Kali Linux
Ettercap is pre-installed in Kali Linux, but if you need to install it manually, you can do so with the following command:
sudo apt-get install ettercap-graphicalUsing Ettercap
Ettercap can be used in both graphical and command-line modes. Below are steps to use Ettercap in both modes for a basic MITM attack.
Graphical Mode
To start Ettercap in graphical mode, use the following command:
sudo ettercap -GFollow these steps for a basic ARP poisoning attack:
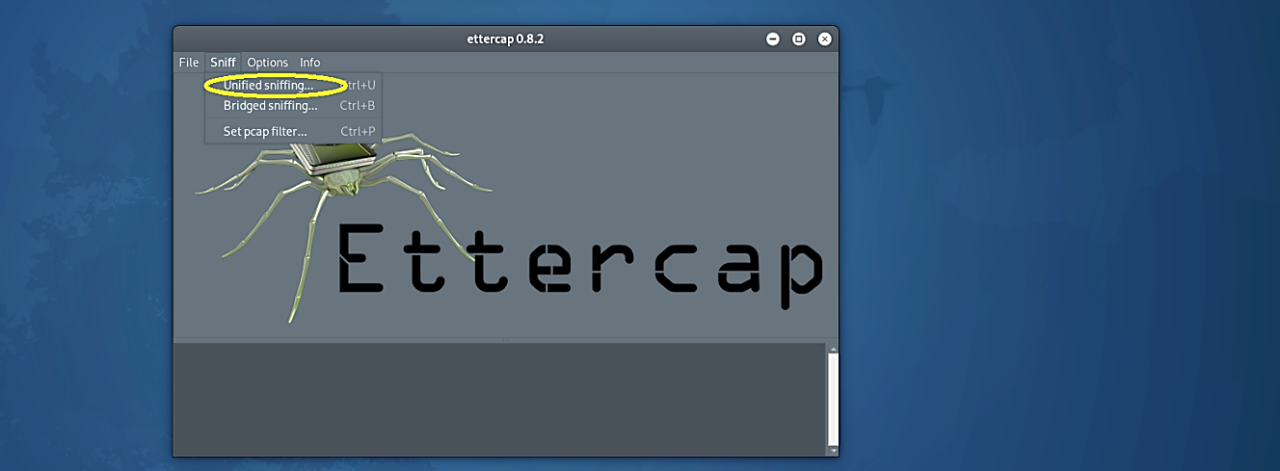
- Open Ettercap in graphical mode.
- Select Sniff > Unified Sniffing.
- Choose the network interface you want to use.
- Go to Hosts > Scan for Hosts.
- After scanning, go to Hosts > Host List to see the detected hosts.
- Select the target machine as Target 1 and the gateway as Target 2.
- Go to Mitm > ARP Poisoning and check Sniff remote connections.
- Start the attack by clicking on the start button or selecting Start > Start Sniffing.
Command-Line Mode
For command-line usage, Ettercap provides a powerful interface:
sudo ettercap -T -i eth0 -M arp:remote /192.168.1.2// /192.168.1.1//In this command:
-T: Text mode (command-line).-i eth0: Specifies the network interface.-M arp:remote: Specifies the MITM attack method (ARP poisoning in this case)./192.168.1.2//: Specifies the target machine./192.168.1.1//: Specifies the gateway.
Learning More About Ettercap
For more detailed information and advanced usage of Ettercap, consider the following resources:
Conclusion
Ettercap is a powerful tool for network analysis and security, offering extensive capabilities for man-in-the-middle attacks. By understanding how to configure and use Ettercap effectively, cybersecurity professionals can better secure networks and conduct thorough penetration testing.