How to use ARP Spoofing and Bettercap Installation, Usage, and Real-World Examples
Comprehensive Guide to ARP Spoofing and Bettercap in Kali Linux: Installation, Usage, and Real-World Examples
Introduction
In the realm of network security, ARP spoofing is a technique used to intercept, modify, or block data packets in a network. Bettercap is an advanced, powerful, and easy-to-use tool to perform various network security tests, including ARP spoofing. This guide will delve into what ARP spoofing is, how it works, and how to use Bettercap in Kali Linux to perform ARP spoofing and other network security tasks.
What is ARP Spoofing?
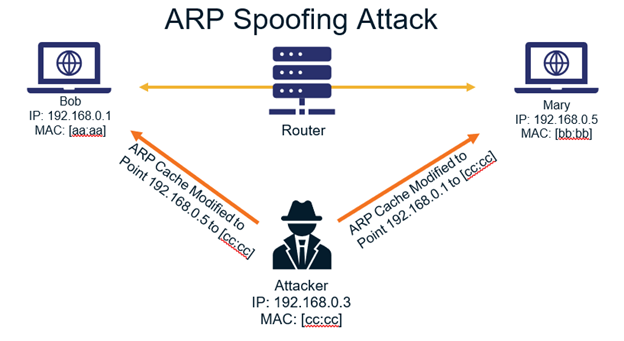
ARP spoofing, also known as ARP poisoning, is a type of cyber attack where the attacker sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of the attacker’s MAC address with the IP address of a legitimate computer or server on the network. Once this association is made, the attacker can intercept, modify, or stop data destined for that IP address.
How Does ARP Spoofing Work?
ARP spoofing exploits the lack of authentication in the ARP protocol. Here’s how it typically works:
- The attacker sends a forged ARP reply packet to the network gateway, associating the attacker’s MAC address with the IP address of a target device.
- The attacker sends another forged ARP reply packet to the target device, associating the attacker’s MAC address with the IP address of the network gateway.
- This creates a scenario where all traffic between the target device and the network gateway passes through the attacker’s device.
Introducing Bettercap
Bettercap is a powerful and user-friendly network attack and monitoring tool that can perform various MITM (Man-In-The-Middle) attacks, including ARP spoofing. It is designed to replace Ettercap and provides advanced features for network analysis and penetration testing.

Installing Bettercap in Kali Linux
Bettercap is included in the Kali Linux repositories and can be installed using the following command:
sudo apt-get install bettercapUsing Bettercap for ARP Spoofing
Once Bettercap is installed, you can use it to perform ARP spoofing with these steps:
Step-by-Step Example for ARP Spoofing
Here’s a practical example of performing ARP spoofing on a network using Bettercap. We’ll use two devices on the same Wi-Fi network: a Kali Linux machine (attacker) and another computer (target).
1. Start Bettercap
Open a terminal on your Kali Linux machine and start Bettercap with the following command:
sudo bettercap -iface wlan02. Enable ARP Spoofing
In the Bettercap interactive session, enable ARP spoofing by running:
set arp.spoof.fullduplex true
set arp.spoof.targets [target_IP]
arp.spoof onReplace [target_IP] with the IP address of the target machine you want to spoof.
3. Sniff Network Traffic
To start sniffing network traffic, use the following command:
net.sniff onHow to Know if ARP Spoofing Works
On the target machine, you can check the ARP table to see if it has been poisoned. On a Windows machine, use the following command in Command Prompt:
arp -aOn a Linux machine, use:
arp -nIf the MAC address for the network gateway’s IP address matches the attacker’s MAC address, ARP spoofing is successful.
Using Bettercap for DNS Spoofing
Another common attack performed with Bettercap is DNS spoofing. Here’s how you can do it:
Step-by-Step Example for DNS Spoofing
Follow these steps to perform DNS spoofing:
1. Start Bettercap
Open a terminal on your Kali Linux machine and start Bettercap with the following command:
sudo bettercap -iface wlan02. Enable DNS Spoofing
In the Bettercap interactive session, configure DNS spoofing by running:
set dns.spoof.all true
set dns.spoof.domains [target_domain]
set dns.spoof.address [fake_IP]
dns.spoof onReplace [target_domain] with the domain you want to spoof (e.g., example.com) and [fake_IP] with the IP address you want to redirect the target to.
3. Sniff Network Traffic
To start sniffing network traffic, use the following command:
net.sniff onHow to Know if DNS Spoofing Works
On the target machine, try to access the spoofed domain (e.g., example.com). If it redirects to the fake IP address specified, DNS spoofing is successful.
Learning More About Bettercap
For more detailed information and advanced usage of Bettercap, consider the following resources:
Conclusion
Understanding ARP spoofing and using Bettercap in Kali Linux are essential skills for network security professionals. Bettercap’s robust and versatile toolkit allows for comprehensive network analysis and penetration testing, making it a valuable asset in securing networks against various attacks.